Jenkins

|
|
|
If you are using the Jenkins pipeline for development automation, you can integrate it with Bright to run security scans on every new build within your development environment. Depending on the use case, you can apply multiple options for running scans from your CI/CD pipeline. |
Use cases
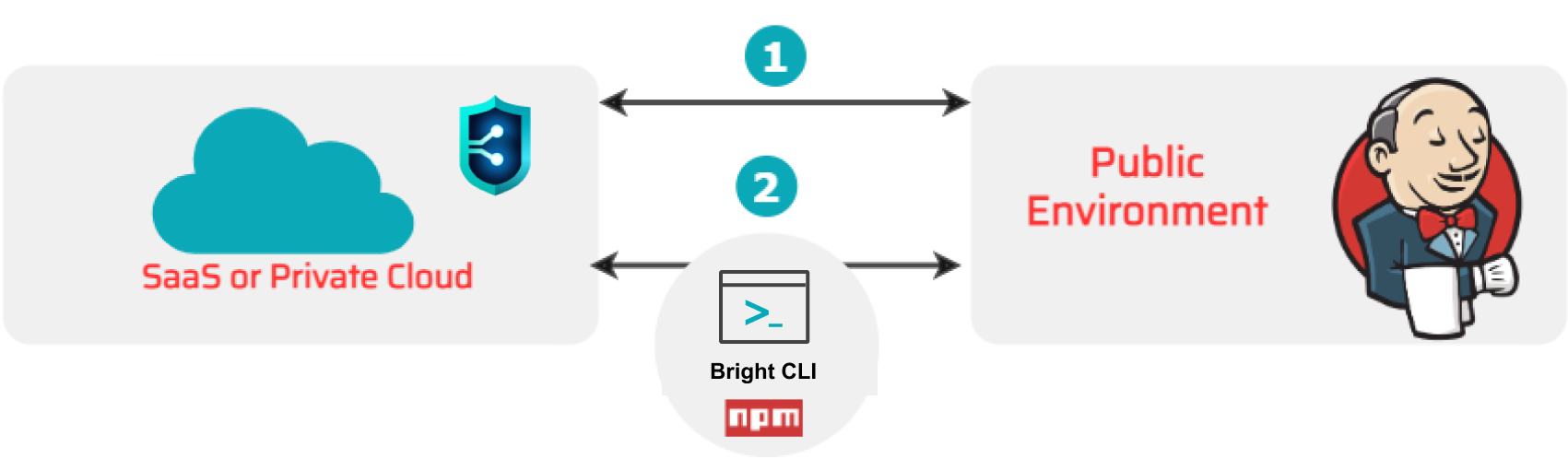
Scanning a target in public environment
Upon a release of a new build, you can run an overall complete scan of the target in the production or public pre-production environment. In this case, long scans will not interfere with the development process as compared to scanning in a private environment.
Depending on the access to the deployed target, you can run a scan using multiple options.
 Directly from the Bright app.
Directly from the Bright app. From your pipeline using the Bright CLI (NPM). Find the example here.
From your pipeline using the Bright CLI (NPM). Find the example here.
Scanning a target in a private environment
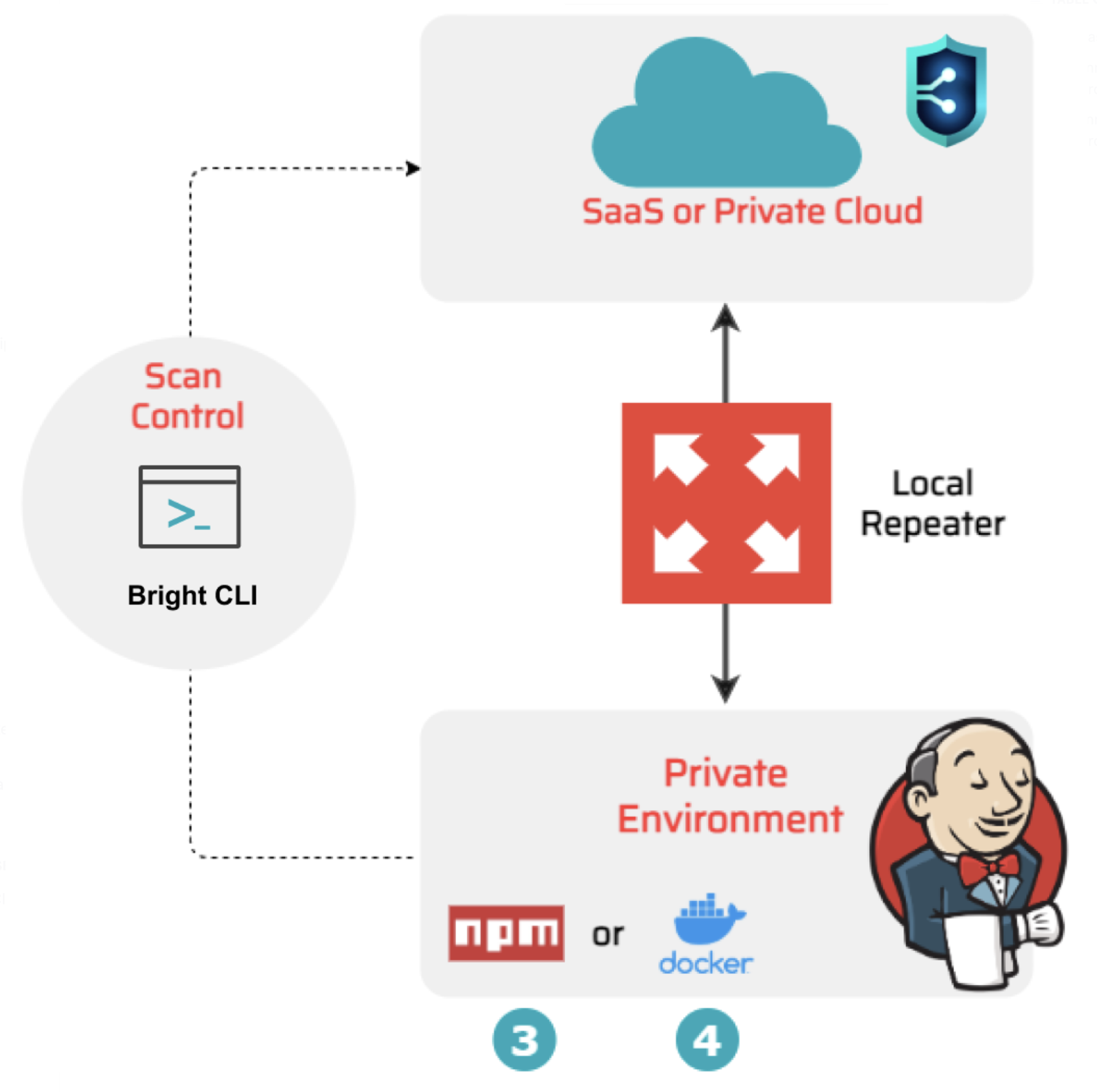
You can run fast scans of the application which is currently under development within your pipeline. Bright allows you to follow the fail-fast principle by interrupting a scan automatically at the first detected vulnerability. Using this option, you are able to quickly and timely find and fix the security issues at the build level without delaying the whole development process.
As the scan target is closed within your pipeline, the Bright engine cannot access it directly from the cloud. In this case, you can use a Repeater which serves as a request-proxy between Bright and a scan target inside your private environment. You should first register (create) the Repeater in the Bright app, and then connect it to your pipeline using the generated Repeater ID.
To run scans directly from your pipeline, you need to install the Bright CLI. It provides an easy-to-use interface and multiple commands you can use in your Jenkins flow.
You can either run the Bright CLI with a Repeater using ![]() the NPM or by installing
the NPM or by installing ![]() the Bright's Docker image inside your pipeline.
the Bright's Docker image inside your pipeline.
Find the examples here:
Updated 7 months ago