Scanning at the Enterprise Level
The Repeater mode of the Bright CLI is the best solution for organizations that cannot open a port in the firewall for inbound traffic or expose targets externally. If the scan target is closed within a private company network, the Bright engine cannot access it directly from the cloud, and in this case the Repeater will serve as a request-proxy between the Bright cloud engine and the scan target inside your private network. You can either connect a central Repeater to the entire network to run all scans through it, or connect multiple Repeaters to use them separately, for each specific project.
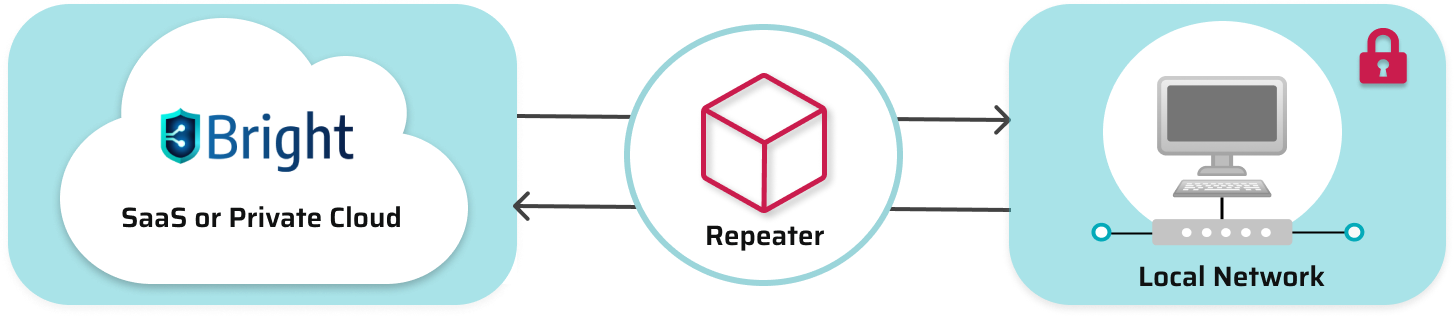
Below you can find the following examples of running scans in the Repeater mode:
- Scanning using the Repeater deployed on a cloud instance (VM)
- Scanning in the Repeater mode, via a custom proxy
Scanning using the repeater deployed on a cloud instance (VM)
To scan a target in your local network (behind a firewall) in the Repeater mode, you can deploy the Repeater locally on your machine or use your cloud provider instead (for example, AWS, Azure, and so on).
When deployed locally, the Repeater disconnects once you close the console, shut down the machine, or in case of a network failure. If the Repeater disconnects during a scanning process, the scan will fail automatically. By running the Repeater on a cloud instance (VM), you decrease the risk of accidental disruption of a scan. This also allows you to use the Repeater as an “always-on” option.
To deploy the Repeater on a cloud instance, you first need to create the instance. The process of instance creation differs for all cloud providers. Please see the documentation of your cloud provider for the instructions. For example, if you are using AWS, the instructions can be found here.
Once the instance is launched, you need to install the Bright CLI on it, using the NPM or Docker option. The installation option depends on the instance OS. Find the CLI installation guide for your OS type under the Repeaters Overview section. Before proceeding, verify the prerequisites have met.
Prerequisites
- You have launched a cloud instance (VM).
- You have installed the Bright CLI on it. The installation option depends on the instance OS. Find the CLI installation guide for your OS type under the Repeaters Overview section.
- You have created a Repeater and have a valid API key. See the prerequisites page for additional details.
Run the Repeater
Activate the Repeater on the cloud instance:
brightsec-cli repeater --token $AUTH_TOKEN --id $REPEATER_ID --cluster https://app.brightsec.com
Note
- Sample variables are marked with a
$. You must substitute them for your real values.- If you are using the Bright app on a private cloud, ensure you specify the custom cluster instead of
<https://app.brightsec.com> (for example,<https://my-cluster.brightsec.com>).
Scanning in the repeater mode, via a custom proxy
You can scan a target in your local network so that all requests from the Bright cloud are securely pulled via your custom proxy, in the Repeater mode. This also allows you to monitor all the traffic used for scan-related communication between the Bright engine, Repeater, and local target. You can configure the protocol to only proxy either the internal (from the Repeater to the local target) or external (from the Repeater to the Bright engine) traffic.
To scan in the Repeater mode, you first need to register (create) the Repeater in the Bright app, and then connect (activate) it using the generated Repeater ID.
Prerequisites
- You have installed the Bright CLI. The installation option depends on the instance OS. Find the CLI installation guide for your OS type under the Repeaters Overview section.
- You have created a Repeater and have a valid API key. See the prerequisites page for additional details.
Run the Repeater
Activate the Repeater and connect it to your proxy - this will proxy the traffic to the targets and to Bright:
bright-cli repeater --token $AUTH_TOKEN --id $REPEATER_ID --proxy $SOCKS_URL --cluster https://app.brightsec.comHere is an example of the proxy format: --proxy socks5://1.1.1.1
- If you want to only proxy the traffic to the targets, then use the following command:
bright-cli repeater --token $AUTH_TOKEN --id $REPEATER_ID --proxy-target $SOCKS_URL --cluster https://app.brightsec.com- If you want to only proxy the traffic to Bright, then use the following command:
bright-cli repeater --token $AUTH_TOKEN --id $REPEATER_ID --proxy-bright $SOCKS_URL --cluster https://app.brightsec.com
Notes:
- Bright supports SOCKS4, SOCKS5, SOCKS4a, and SOCKS5h. If you specify
SOCKS://<URL>, SOCKS5h is applied by default.- If you are using the Bright app on a private cloud, ensure you specify the custom cluster instead of
<https://app.brightsec.com> (for example,<https://my-cluster.brightsec.com>).
Updated 11 days ago