Entrypoints
Bright provides a user-friendly feature that simplifies the editing of Baseline values. This functionality replaces parsed values with placeholders, making it quick and convenient to modify them. It applies to both dedicated Discovery and the Legacy scan. The Crawler uses the Engine's information to match the Baseline values.
This approach offers the following benefits:
- Comprehensive visibility of the current baseline values and any connectivity issues for each Entrypoint.
- The ability to edit and test Baseline values before initiating scans, ensuring accuracy and efficiency.
- Preservation of optimal baseline values between scans, allowing for consistent and reliable results.
Users have the flexibility to edit these values themselves through the Parameter view. Auto-matched values are labeled as Auto-filled, prompting users to consider modifying the suggested values if needed. When an entrypoint as created manually, all baseline values are automatically categorized as manually added without additional highlighting.
Fixing the entrypoint
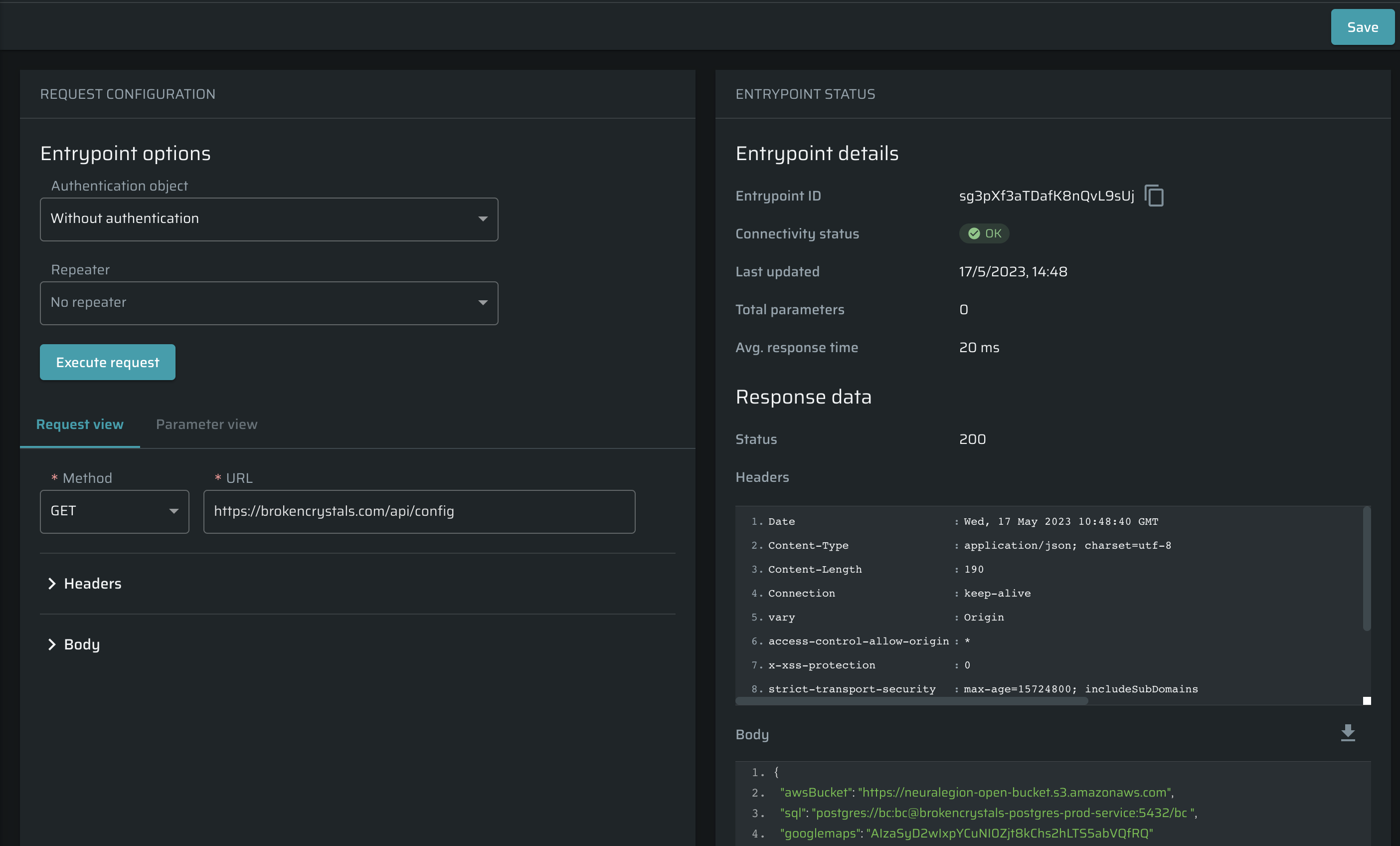
Using this tool, it's possible to fix the connectivity status of the entrypoint. To do that, find the entrypoint with a connectivity issue, and then click Edit.
Now you can use the Parameter view tab to change baseline values to locate a problem and fix it.
Once a request is executed, baseline values are extracted and then replaced with placeholders in the raw request. The Parameters tab allows users to manage values without changing the configuration of the request.
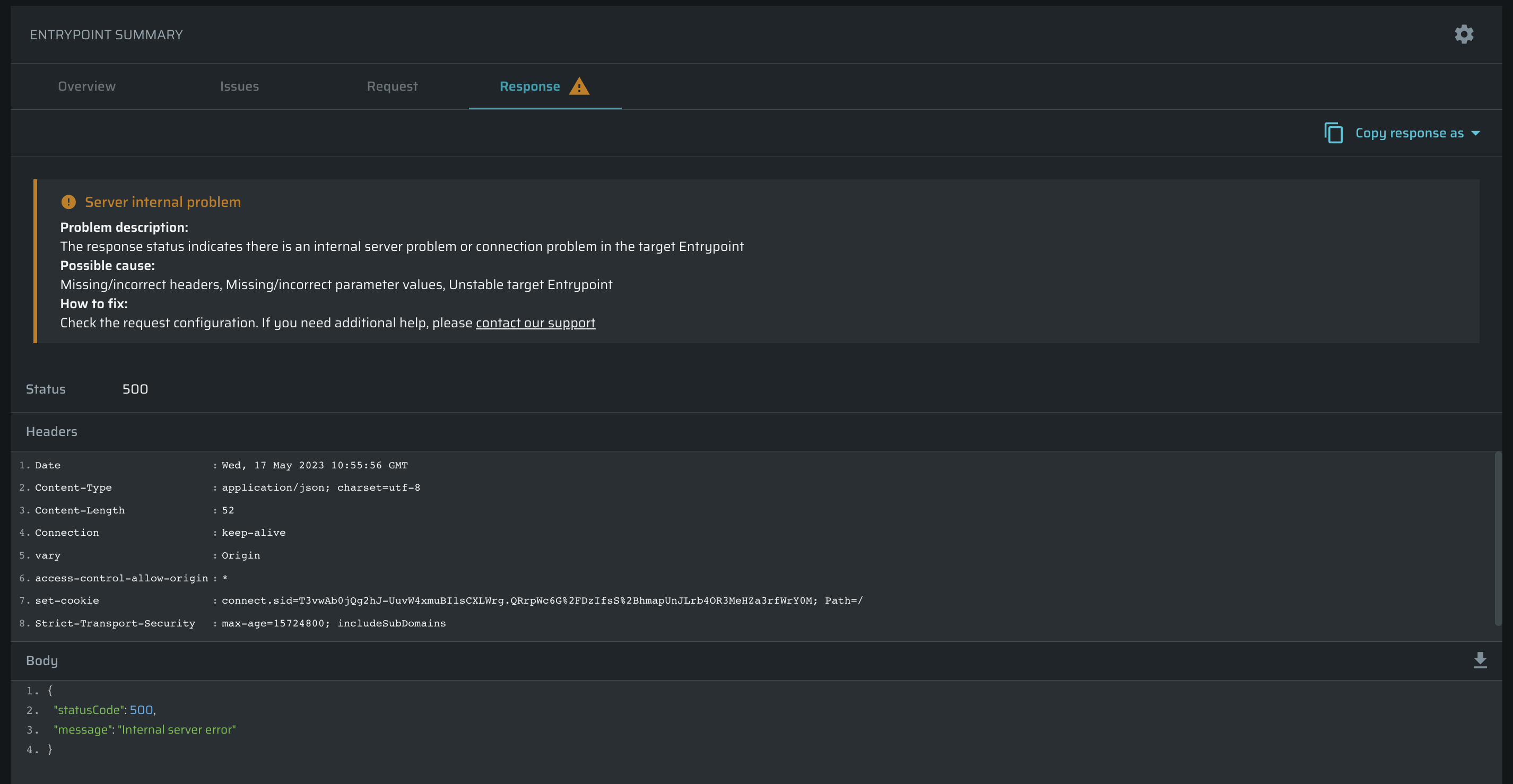
Click Execute request to test the entrypoint. Results will appear in the Entrypoint status table. Once the connectivity status is OK, click Save to apply changes.
Editing an existing Entrypoint
To edit an existing entrypoint, do the following:
- Open Projects → Entrypoints →
 → Edit entrypoint
→ Edit entrypoint - Change the data in the Request configuration tab
- Click Execute request to test the entrypoint.
- Click Save to finish editing
Re-discovery can override the parameters changes made before.
Updated about 2 months ago
