Issues Summary
This page contains information about the discovered issues. To open this page, do the following:
- Open Projects tab.
- Select a project.
- Open the issue from the Project Overview block.
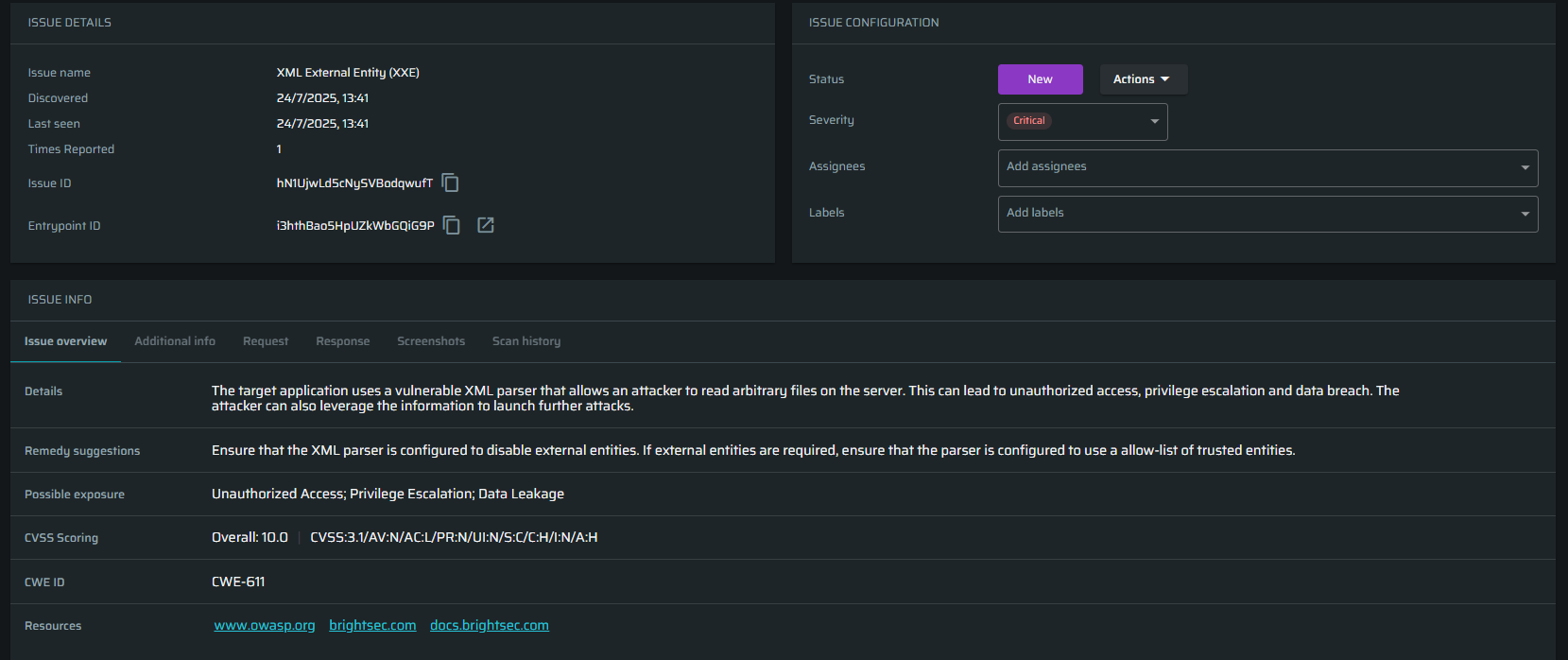
Issue details
This block contains the basic issue information, including Issue ID and Entrypoint ID. Click ![]() to open the entrypoint summary page in a new tab. To copy the Issue ID or the Entrypoint ID, use
to open the entrypoint summary page in a new tab. To copy the Issue ID or the Entrypoint ID, use ![]() button.
button.
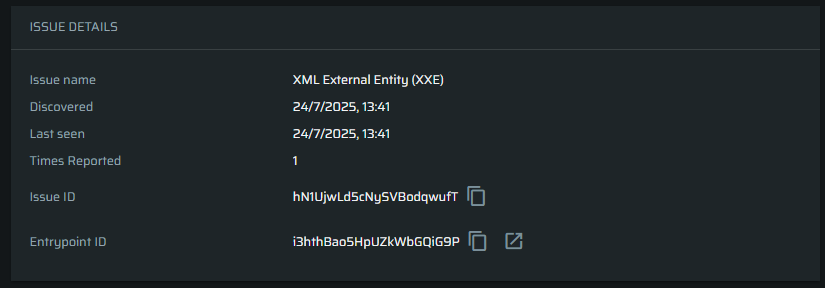
Issue configuration
This widget allows users to manage the issue, changing its status and severity, adding or deleting assignees, and managing issue labels.
-
To change the status of the issue, click Actions and select an action to perform. Using this menu the issue can be immediately resolved, reopen, or ignored.
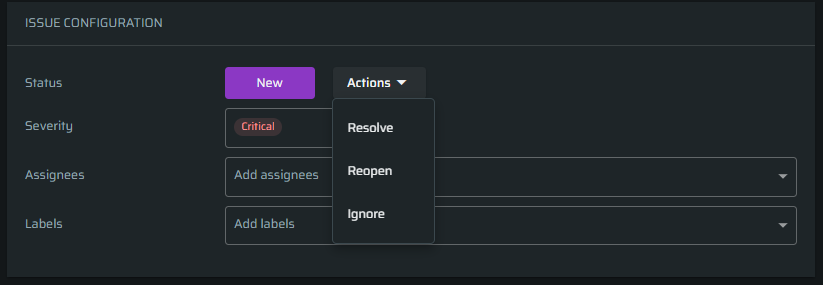
-
To change the issue severity, open the relevant menu and select an appropriate status manually from Critical, High, Medium, or Low.
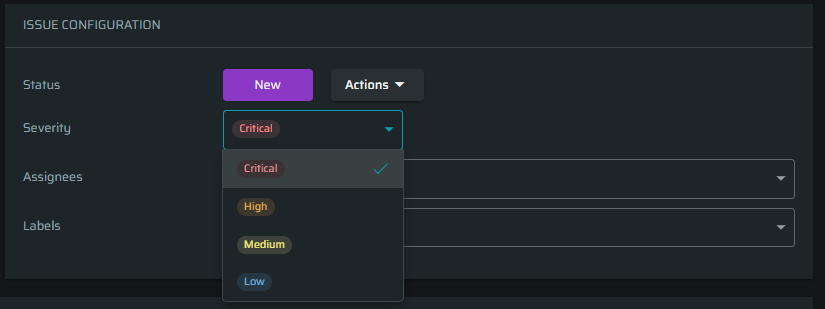
-
To add an assignee to the issue, start typing the name and then select it from the menu. If you want to share the issue between all assignees, select All option.
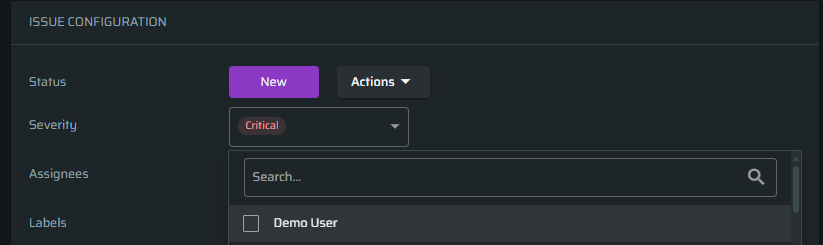
-
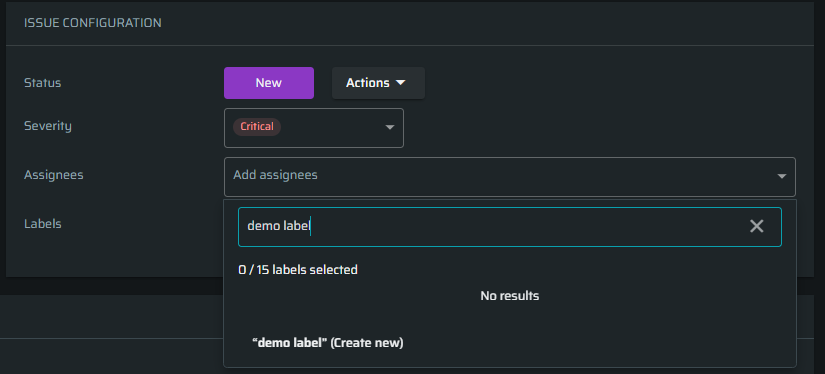
To add a label to the issue, start typing the name and then select it from the list. If you want to create a new one, click the button Create new below the search results.
Issue info
This block contains detailed information about the issue and divided into the following tabs:
-
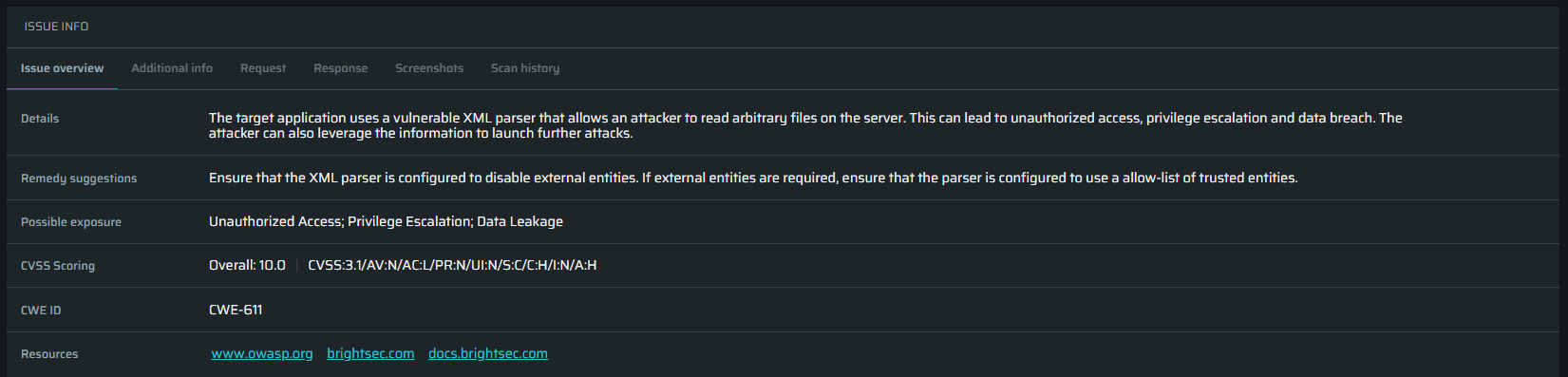
Issue overview:
- Details – Provides a short description of this issue. It also displays dynamically generated information about what happened at the bottom of the explanation.
- Remedy Suggestions – Provides a short explanation about how this issue should be fixed.
- Possible Exposure – Provides a brief non-technical explanation about what kind of impact this specific issue might have on the application in case of a malicious breach.
- CVSS Scoring – Provides a Common Vulnerability Scoring System score summarizing this specific issue.
- CWE-ID – Provides a Common Weakness Enumeration ID number of this specific issue.
- Resources – Provides references to resources in case more detailed explanations are required.
-
Additional info - Available for some of the vulnerabilities and adds an additional context (like the underlying OS, CSRF vector, etc.).
-
Request - Shows the request and the adjusted part used for the attack simulation. You can copy the request or parts of it for reproduction by clicking Copy request as.
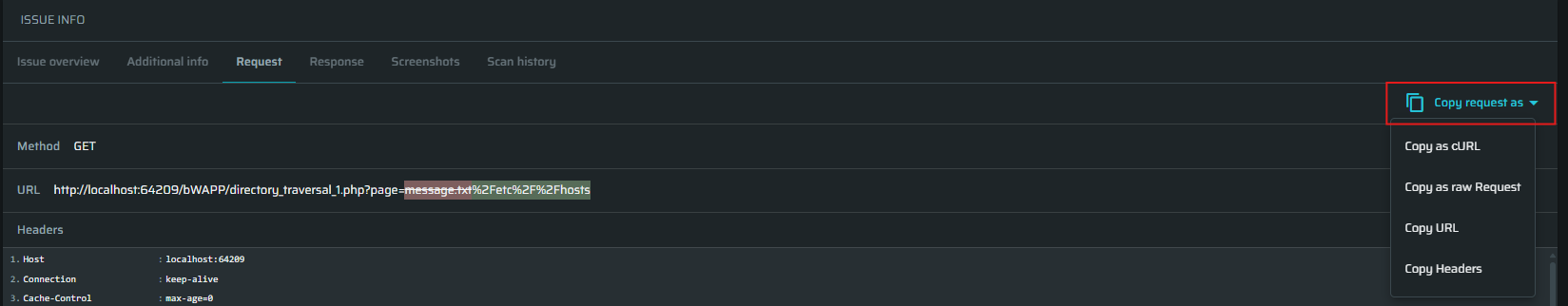
-
Response - Shows the response we received from the target. You can copy the response or parts of it by clicking Copy response as. If the response has a large body, you can click the Show response body button to show it, or click on the buttons to the right of it to copy or download it.
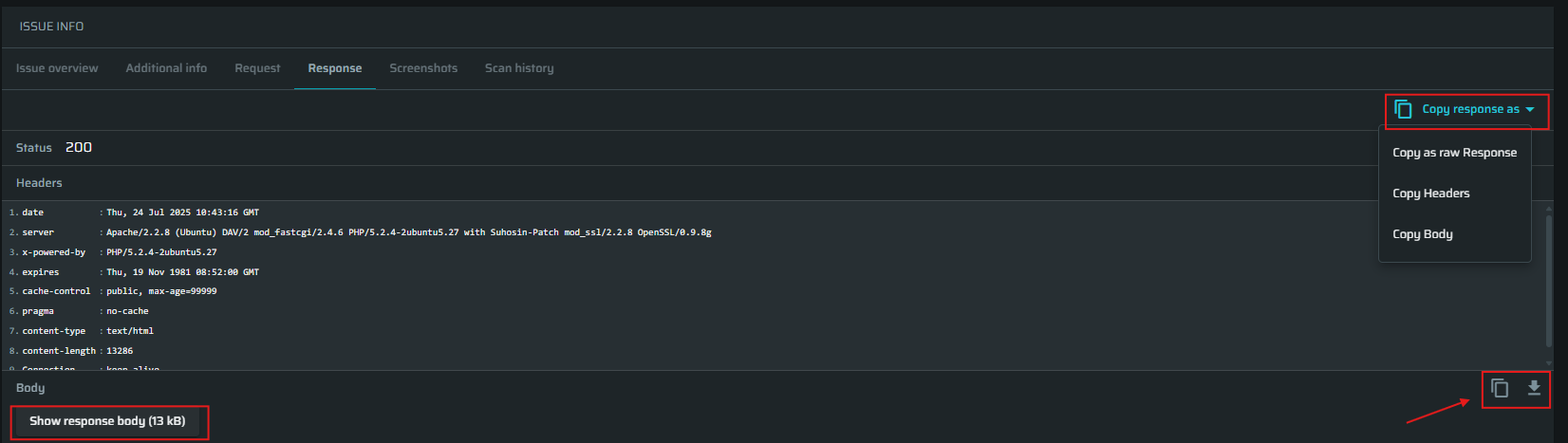
-
Screenshots - Available for frontend vulnerabilities and shows visual evidence of the vulnerability (like unvalidated redirects. You can click the image to see it in large.
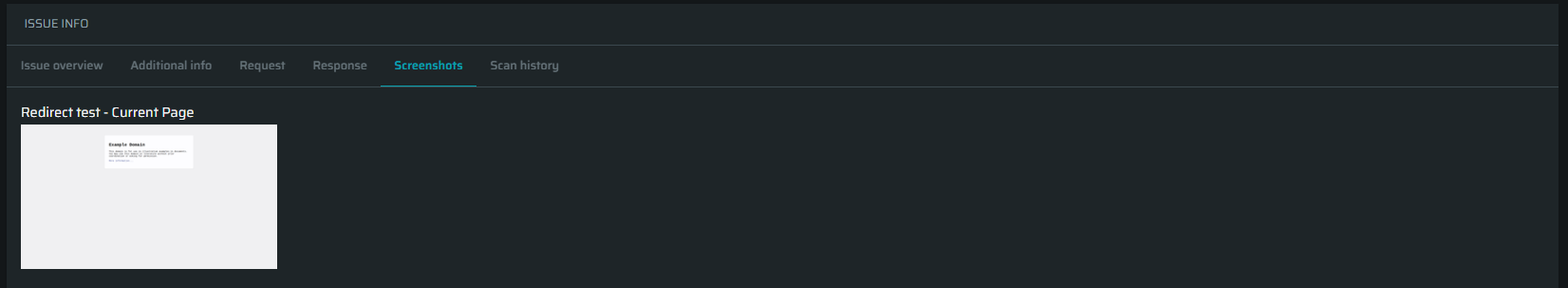
-
Scan history: Shows all scans where the particular issue was presented before. Click
 button to open a related scan in a new tab.
button to open a related scan in a new tab.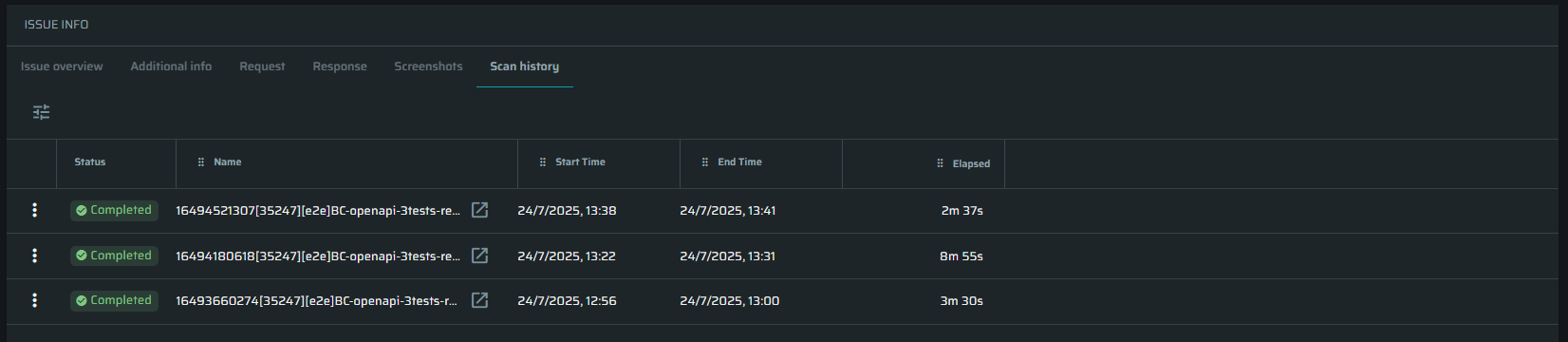
Updated 7 months ago