Configuring OIDC Connect (OAuth)
Before following the instructions below, ensure that your application and authenticated resources are accessible to the Bright engine, either directly from the Internet or via the Repeater.
The OIDC (OAuth) authentication method is designed to configure the standard OAuth 2.0 flow, which requires the use of client or user secrets.
Currently, only the Customer Credentials and Resource Owner Password grant types of OIDC are supported.If your application is using PKCE, please use the Recorded Browser-Based Form Authentication or Manual Browser-Based Form Authentication authentication options.
From the Authentication type dropdown list, select OpenID Connect (OAuth), and then proceed to the authentication details.
Authentication details
In this section, complete the provided fields to set up a valid authentication request for the end-point API.
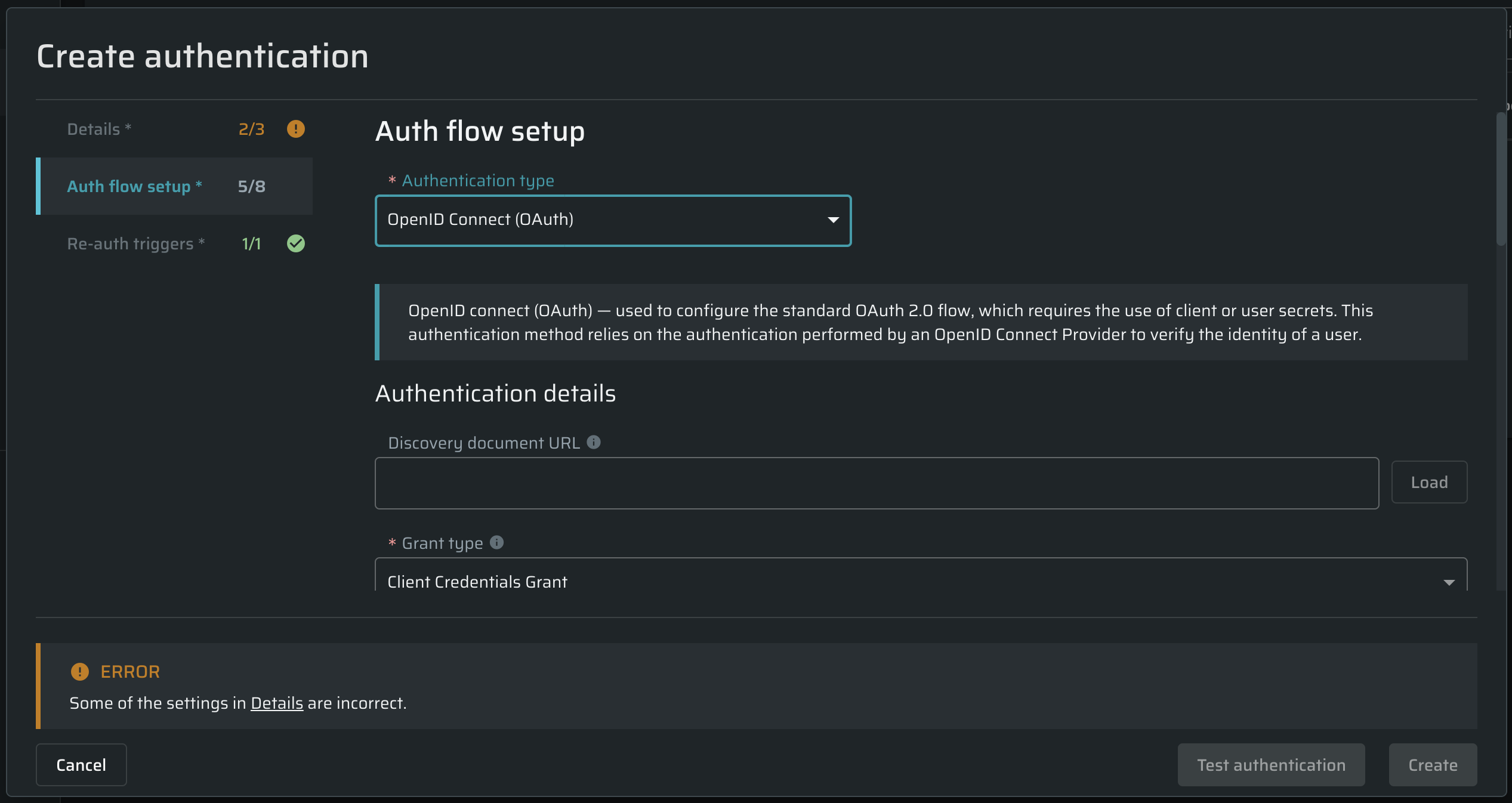
Field | Guidelines |
|---|---|
Discovery document URL | Provide a discovery document URL (https://your_host/.well-known/openid-configuration) to populate endpoint URLs automatically or leave this field empty to enter endpoint URLs manually. |
Grant type | From the drop-down list, select the grant type you need:
|
Token Endpoint | Obtain an access and/or ID token by presenting an authorization grant or refresh token. |
Client ID | Enter your application client ID, a unique client identifier preregistered in OpenID Provider. |
Client Secret | Enter your application client secret, which is used to authenticate to the Token Endpoint. |
Scope | (Optional)_ Enter a space-separated list of scopes. |
Resource | (Optional)_ Enter a line-separated list of resources. |
Audience | (Optional)_ Enter the intended recipient of the token. |
Embed in | Select where to embed the token in the request.
|
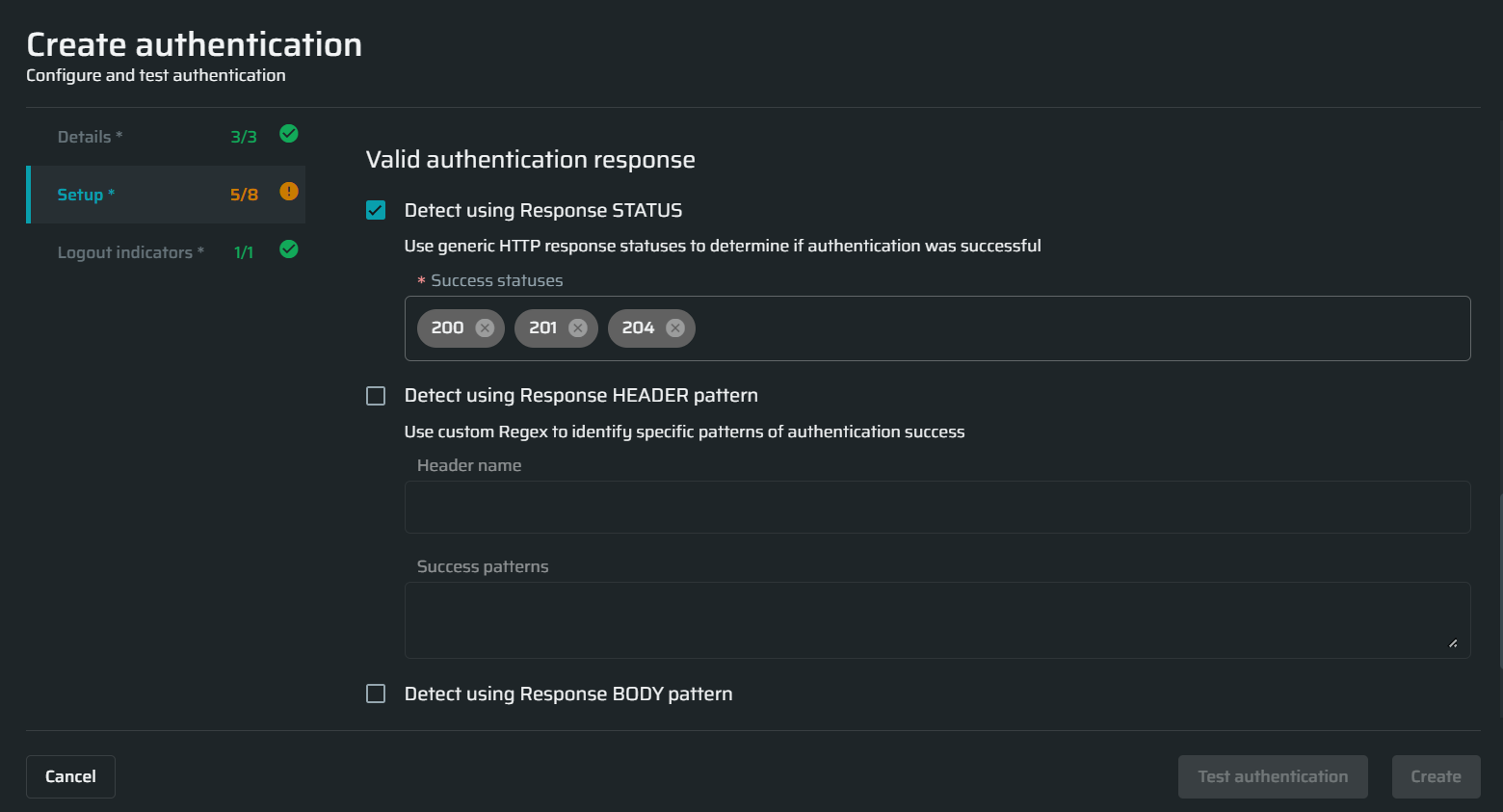
Valid authentication response
In this section, select the options you want to use during the application scanning to determine that the authenticated resource has been reached. The options define how the application responds if a full authentication flow passes successfully.
Updated 7 months ago