Repeater
Overview
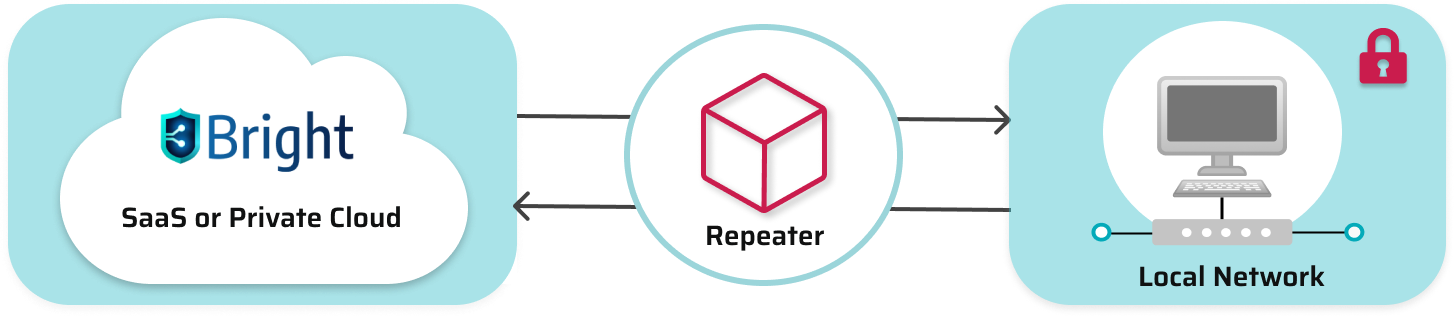
The Bright Repeater is a scan proxy which provides a secure connection between the Bright cloud engine and a target on a local network. The Repeater mode enables you to securely scan targets on a local network, without having to allowlist the Bright IP address in your firewall for incoming traffic.
The Repeater mode is designed for:
- Organizations that cannot open a port in the firewall for inbound traffic. A Repeater enables you to scan either from the Bright SaaS or a private cloud.
- Users who must run a local scan on their machine without deploying the target application.
Important
- To function properly, a Repeater must have an outbound connection to amq.app.brightsec.com via the AMQ protocol (over TLS) using port 5672.
- If your environment uses a proxy server, please make sure that the SOCKS protocol support is enabled.
- If traffic from a Repeater to the scan targets is unstable or slow (under 100 milliseconds), this may result in Disrupted Scans and missed vulnerabilities. To avoid such situations, we recommend that you install the Repeater on a production grade machine with a fast and stable connectivity to the targets. You should also avoid connecting the Repeater through a VPN, mobile-hotspot or similar slow/unstable connections.
- The Repeater mode is not compatible with TLS tests
A Repeater is not required if you are able to allowlist a specific IP and port in your firewall.
How the repeater deployment works
The Bright Repeater is an open source scan proxy which securely connects to the Bright cloud engines and mediates all traffic from the cloud to any local target.
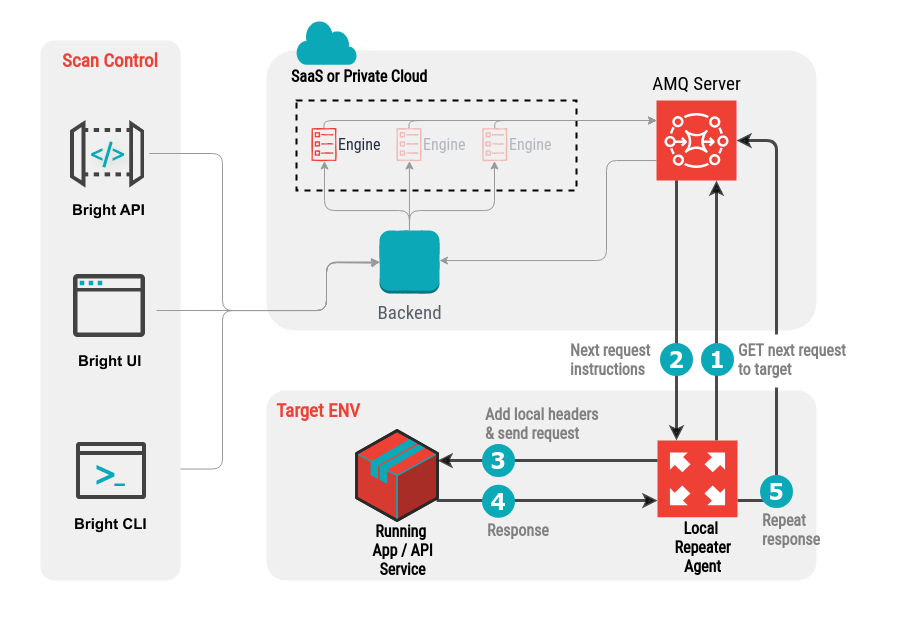
After starting a scan in the Repeater mode, communication works as follows:
- The Repeater initiates a GET request to the cloud engine via the AMQ server.
- The Repeater receives the request instructions describing how to interact with the local target.
- The Repeater locally adds the relevant headers to the request, such as authentication headers, and sends the request to the local target.
- The local target returns the response to the Repeater.
- The Repeater sends the response to the engine.
- The Repeater returns to #1 until the scan completes.
Technical requirements
Connecting a Repeater requires:
- A local machine with:
- System: Ubuntu OS / Windows 8+ / MacOS / Docker 20+
- Processor: x86 or x64 1 core (minimum), 2 core (recommended)
- RAM: 512 MB (minimum), 1 GB (recommended)
- Hard disk: up to 512 MB of available space may be required
- The Docker compose: v20+
- NodeJS: v10+, not higher than 18 (minimum), v14, v16, v18 (recommended)
- Access to the relevant internal targets on a local network
- Access to
amq.app.brightsec.comonport 5672or a private cloud on the relevant port - If a proxy server is used, make sure it is configured to allow the SOCKS protocol. The Bright Repeater does not support HTTP/HTTPS proxy protocols.
Installation
To run a scan in the Repeater mode so that all scan requests are pulled (as outbound traffic) from the Bright cloud through a Repeater to the local target, you first need to install the Bright CLI on your machine. Using a special Bright CLI command, you will be able to connect a Repeater to your local network.
See the Bright CLI installation guide for the instructions.
Usage
For the usage examples, see Getting Started.
Getting a Repeater ID
To continue, you need to adjust a repeater ID. To do so, do the following:
- Open Repeaters tab
- Select particular Repeater, and then click
 to open a menu
to open a menu - Click Copy repeater ID
Updated about 2 months ago
