Release on March 11, 2024
March 11th, 2024
-
Client-side attacks
- Cross Site Scripting (XSS) (High-severity, #3 in the OWASP Top 10), is a type of security vulnerability commonly found in web applications. It occurs when an attacker injects malicious scripts into web pages.
There are three main types of XSS attacks: Stored XSS, Reflected XSS, and DOM-Based XSS.
In this release, we focused on Reflected XSS and DOM-Based XSS.
In this release, we’ve:- Introduced the DOM Based XSS vector into the attack, expanding detection capabilities.
- Enhanced Reflected XSS payloads to detect additional vulnerabilities.
- Optimized the execution time of XSS tests up to 200% (a scan that used to take 6 hours can be completed in 3 hours).
Reflected XSS occurs when an attacker sends a malicious script to a user through a link that appears legitimate.
When the user clicks on the link, the user's browser runs the malicious script.
The DOM Based XSS is a client-side vulnerability that uses a manipulation of the Document Object Model (DOM). The DOM contains the web page's structure as it is displayed in the browser. The DOM defines where text, images, links, and other elements are placed. When an attacker adds a script to a DOM object, it will seem to the user as part of the application, though this content was not sent from the application server. This technique can be used for social engineering, getting secret information from the user, or sending the user to a malicious site.
OWASP: Cross Site Scripting (XSS)
- Cross Site Scripting (XSS) (High-severity, #3 in the OWASP Top 10), is a type of security vulnerability commonly found in web applications. It occurs when an attacker injects malicious scripts into web pages.
-
Server-side attacks
- Cross-Site Request Forgery (CSRF) (Medium-severity, # 1 in the OWASP Top 10), is an attack that occurs when a malicious site you visit makes a request to another site where you're logged in, using your credentials without authorizing it. For example, requesting to transfer funds, changing passwords, etc.
The test generated some false positive alerts that were addressed and improved the test accuracy.
OWASP: Cross Site Request Forgery (CSRF)
- Cross-Site Request Forgery (CSRF) (Medium-severity, # 1 in the OWASP Top 10), is an attack that occurs when a malicious site you visit makes a request to another site where you're logged in, using your credentials without authorizing it. For example, requesting to transfer funds, changing passwords, etc.
-
Discovery
- We continued to optimize our crawling capabilities to shorten the crawling duration. Many variables affect crawling speed. Overall, through multiple benchmark tests, we improved the crawling time between 10% to 20%.
-
GraphQL introspection
-
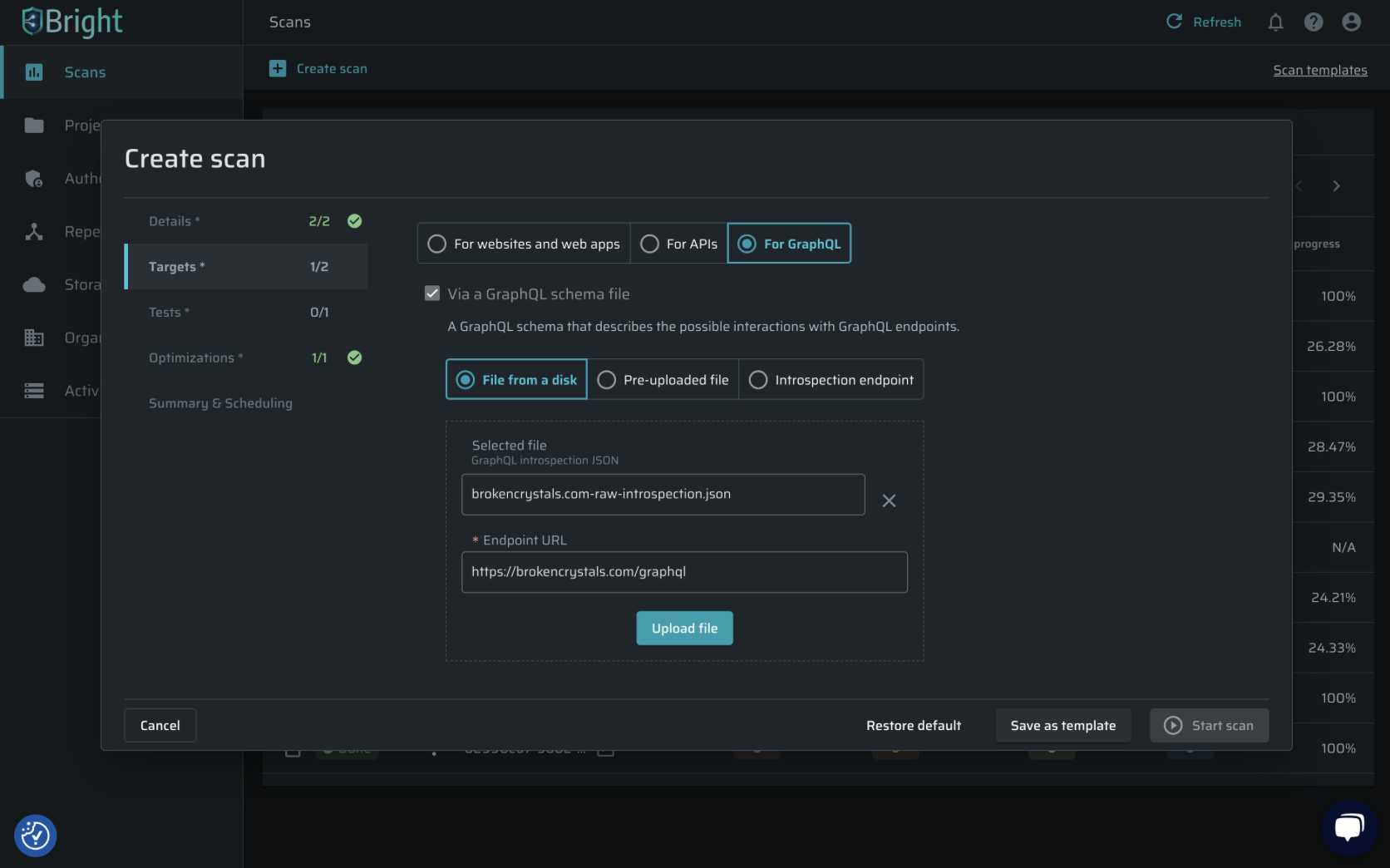
The GraphQL Introspection feature allows users to query the schema and discover the available queries, mutations, subscriptions, types, and fields in a specific GraphQL API.
We've added support for GraphQL introspection and uploading a GraphQL Schema directly, accelerating GraphQL API targets testing definition and improving the user experience working with GraphQL. -
In the create scan dialog, there is a new option to point to an introspection file to be used as the source for the scan entry points:
-
-
CLI
- Support for HTTP(S) proxy protocol for outbound and inbound traffic was added. The repeater can be configured to use WebSocket, to enable scans of internal or external targets from within the internal networks.
Previously, we supported only the SOCKS proxy protocol.
Example:
bright-cli repeater --proxy-internal abc.superproxy.io:12345
bright-cli repeater --proxy-external abc.superproxy.io:12345
- Support for HTTP(S) proxy protocol for outbound and inbound traffic was added. The repeater can be configured to use WebSocket, to enable scans of internal or external targets from within the internal networks.
