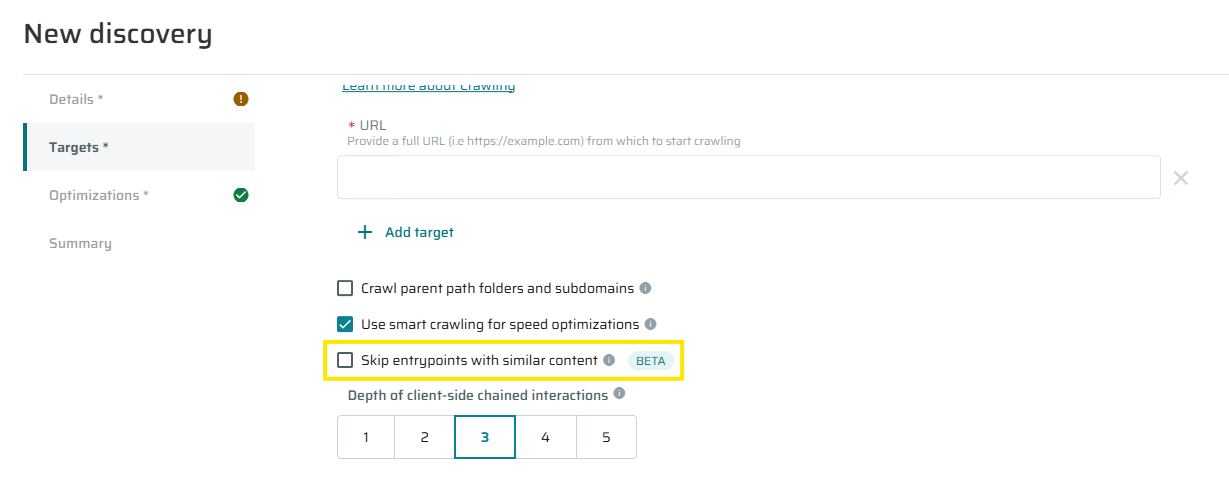
Enhancements
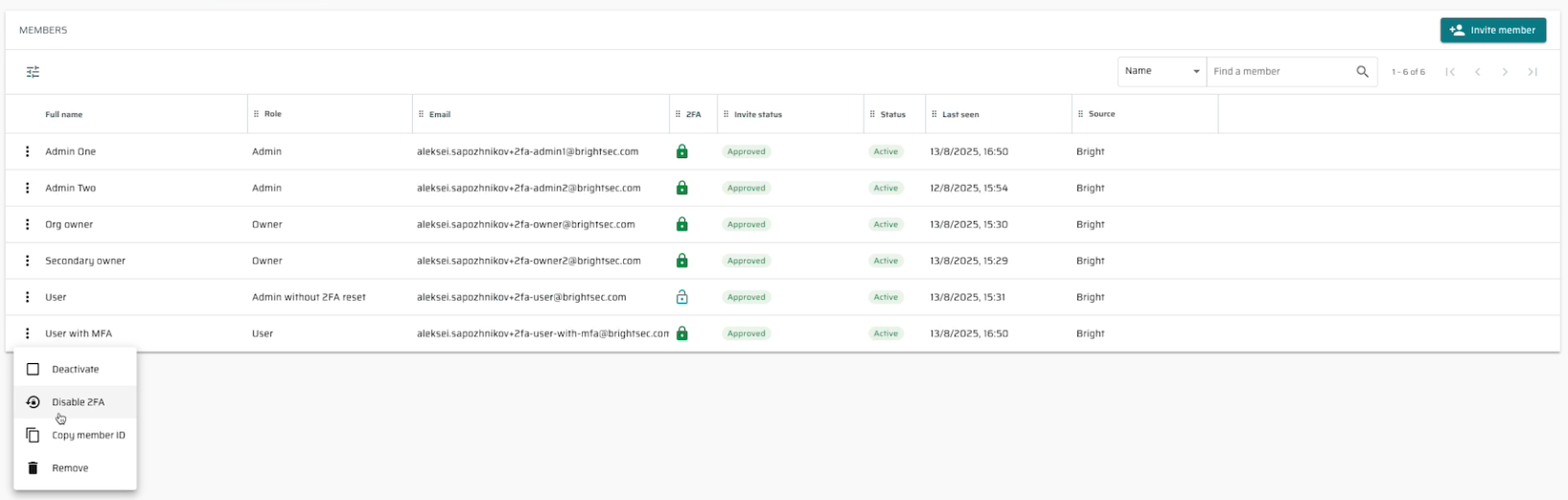
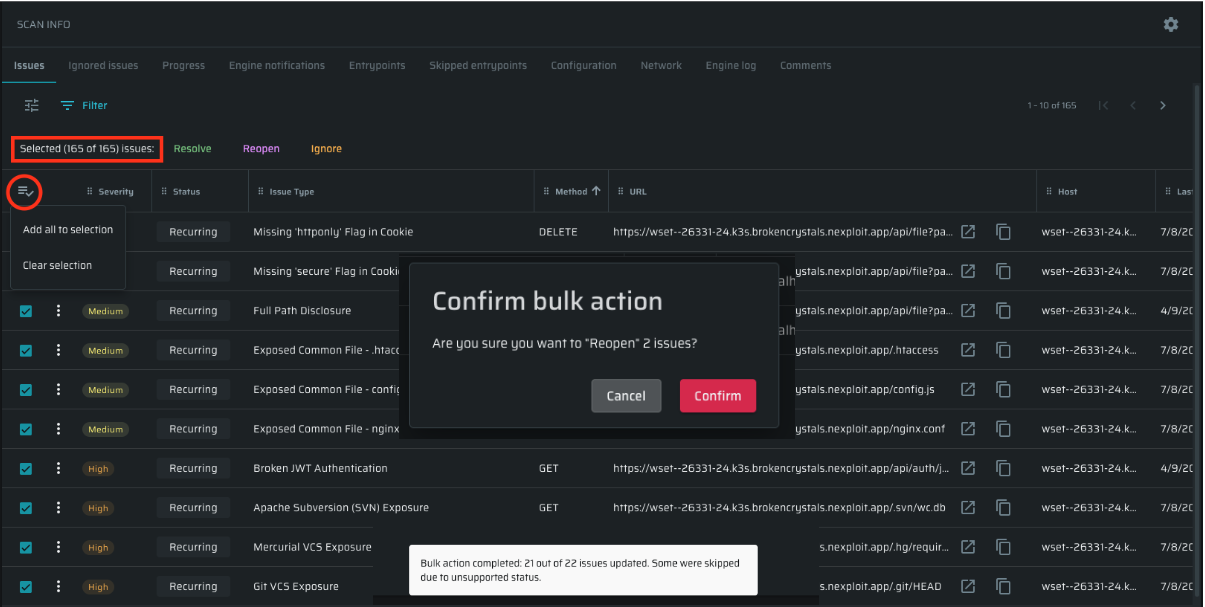
Bulk selection in the status tab
Now you can save time managing large sets of issues inside the Issues table, reduce repetitive work across pages, get clear visibility with a “Selected X of Y” counter, and stay in control with transparent feedback after every bulk action.
What’s new
- Select all across pages - use the "Add all to selection" button to select every issue that matches your current filters, not just the ones on the current page.
- Filter and select - apply bulk actions to only the issues that match your chosen filters.
- Clear selection- reset your choices instantly with the "Clear selection" button.
- Selection counter - always see how many issues you’ve selected out of the total.
- Smarter bulk actions - bulk actions (Resolve, Reopen, Ignore) apply only where they are supported. For example, “Reopen” will affect only resolved issues.
- Confirmation & feedback - before applying an action, you’ll see a confirmation window. Once complete, a notification shows exactly how many issues were updated and if any were skipped.
How it works
- If you select issues with mixed statuses, all actions appear, but only relevant ones are applied.
- If you bulk select a single status, only the actions valid for that status will be highlighted.
Updated API Documentation Link
We’ve updated the API docs link in the Help menu (top toolbar). The link now points to the latest V3 API documentation: API docs V3
This ensures you always have quick access to the most up-to-date API references and capabilities.
Simplified Access to Logs
We’ve streamlined log access by removing the unused logs scope. Going forward, only the org.logs scope will be available for viewing organization-wide logs.
What this means for you
- No impact on access - users with the correct roles and API keys will continue to see all log information as before.
- Audit Log unchanged- all Audit Log features remain fully accessible.
- Cleaner permissions - reduced redundancy makes roles and scopes easier to understand and manage.
Fresh Look: Updated Product Logo
We’ve refreshed our product logo to align with our new brand look.