Release of November 18, 2025
Enhancements
Project Dashboard (New)
The new Application Dashboard is now live. It gives you a clean, easy-to-understand view of your project security. You can quickly see the most important alerts, SLA risks, issue trends, and recent scan activity.
You can find more information in the dedicated user guide we created: Click here.
Accessing the Dashboard
- Go to the Projects page.
- Click on the desired project.
- The Dashboard tab opens automatically as the default view.
Navigation Path:
Projects → [Project Name] → Dashboard

Project Page UI Enhancements
We updated the Project page to deliver a cleaner and more intuitive workflow. The project management tab has been moved to the top for improved visibility and easier navigation.
- To start a new scan, go to the Discoveries page and create a Discovery.
- To add Entry Points, visit the Entry Points page.
- To export Issues, Unconfirmed Issues, or Ignored Issues, navigate to the relavent Issues' page and export directly from there.
- To delete a project, go to the settings page and click on the delete button.

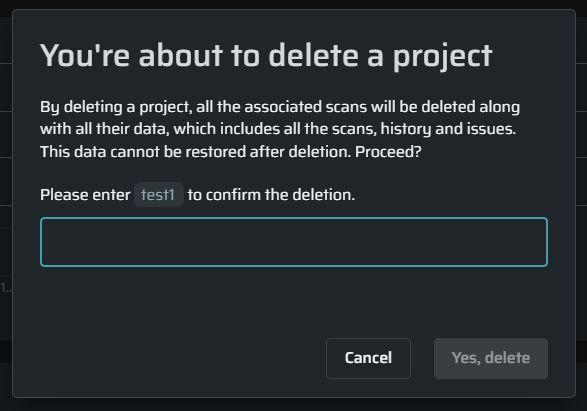
Project Delete Confirmation
To prevent accidental deletions, we added a new confirmation step when deleting a project. Users are now required to type the full project name before deletion is allowed. The Delete button becomes active only when the name is entered correctly, ensuring safer and more deliberate project management.
To delete a project, go to the settings page and click on the delete button.
Mask toggle for Authorized requests setup headers in the Authentication Flow dialog
Header values in the Authorized requests setup section (Advanced tab of the Authentication Flow dialog) can be displayed as Clear text or Masked text. By default, these headers appear as clear text and follow the same masking behavior as other headers in the Authentication Flow.
Note: The unmasking access scope determines who can mask or unmask these header values.

For more information, see Authorized requests setup headers
Bright STAR
STAR GitLab support is now live and available for use
STAR now supports GitLab as a code source, allowing you to run STAR scans directly on your GitLab repositories.
For more information about Bright STAR, see Introducing Bright STAR. To enable STAR in your Bright environment for complete CI/CD auto-testing, remediation, and validation, contact your Bright Customer Success Engineer.
Integrations
Export STAR project issues as SARIF
STAR projects now support export of project issues in SARIF format. This new feature facilitates the seamless sharing of project-level security findings with external tools.
Access and File Details
The new export option is located on the Project Issues screen.
- Go to the Project Issues tab for the STAR project.
- Select the Export menu.
- Choose the new option: Export as SARIF for STAR.
Changes to the SARIF file
The SARIF file keeps the same structure as the existing DAST SARIF export, with one STAR-specific addition in the properties section:
"properties": {
"star_sources": [
"repo-name:branch-name",
"another-repo:another-branch"
]
}New partner integrations: Tenable, Cycode, and Legit
Bright has expanded integration support to connect with three additional security platforms, enhancing visibility and governance across the Software Development Lifecycle (SDLC).
These new integrations let you bring Bright DAST findings into the tools your security and engineering teams already use, so you manage application and pipeline risks from a single place.
Tenable integration (Exposure Management)
Bright connector to Tenable Exposure Management (Tenable One). The connector ingests Bright DAST projects and issues into Tenable as web application assets and findings, using Bright APIs.
With this integration, you can:
- View Bright web application assets together with other Tenable One assets in a single inventory.
- Analyze Bright DAST findings with Tenable’s exposure and vulnerability views, using Tenable’s severity and status mapping.
- Use existing Tenable One workflows—filters, dashboards, and reports—to track and report on Bright-originated issues.
Configuration steps and field mappings for the Bright connector are documented in Tenable Exposure Management. Tenable-Bright connector
Cycode integration (ASPM)
Bright connector to Cycode’s Application Security Posture Management (ASPM) platform. The integration imports Bright DAST findings into Cycode so you can manage web application vulnerabilities together with other AppSec data in a single system.
With this integration, you can:
- Correlate DAST findings with results from other scanners (like SAST and SCA) within CyCode's Risk Intelligence Graph.
- Use Cycode’s dashboards, queries, and workflows to track and triage Bright-originated issues.
- Keep remediation ownership and status aligned across security and development teams.
The integration is configured from the Cycode environment by adding Bright as an external scanner through the Cycode integrations page.
Legit Security integration (ASPM)
Bright connector to Legit Security’s Application Security Posture Management (ASPM) platform. The integration sends Bright DAST findings to Legit so you can manage web application vulnerabilities together with other AppSec data in one place.
With this integration, you can:
- View Bright DAST results alongside findings from other security tools in Legit’s unified ASPM view.
- Use Legit’s workflows, policies, and dashboards to track and remediate Bright-originated issues.
- Keep ownership and status of vulnerabilities aligned between security and development teams.
You configure the integration from the Legit environment by adding Bright as an external security scanner through the Legit integrations page.