Release on April 16, 2024
-
Client-side attacks
- Unvalidated Redirect (Medium-severity, # 1 in the OWASP Top 10) - is an attack that occurs when a website allows users to be redirected to any site specified in the URL path. This could cause the website to redirect the user to a malicious website controlled by an attacker that could be used to steal information or install malware.
- For example, If you visit this link:
https://brokencrystals.com/api/goto?url=www.example.com, you will be automatically taken towww.example.com - In this release, we’ve
Optimized the Unvalidated Redirect test execution duration (from 75 to 30 minutes on Broken Crystals)
-
Server-side attacks
- Cross-Site Request Forgery (CSRF) (Medium-severity, # 1 in the OWASP Top 10) - is an attack that occurs when a malicious site you visit makes a request to another site where you're logged in, using your credentials without authorizing it. For example, requesting to transfer funds, changing passwords, etc.
- OWASP: Cross Site Request Forgery (CSRF)
-
What’s new?
- SameSite is a browser security mechanism that determines when a website's cookies are included in requests originating from other websites.
-
All major browsers currently support the following SameSite restriction levels:
- Strict
- Lax (default)
- None
-
Lax SameSite restrictions mean that browsers will send the cookie in cross-site requests, if both of the following conditions are met:
- The request uses the GET method.
- The request resulted from a top-level navigation by the user, such as clicking on a link.
- In this release, we’ve
Added the SameSite Lux vector, increasing the number of CSRF findings
-
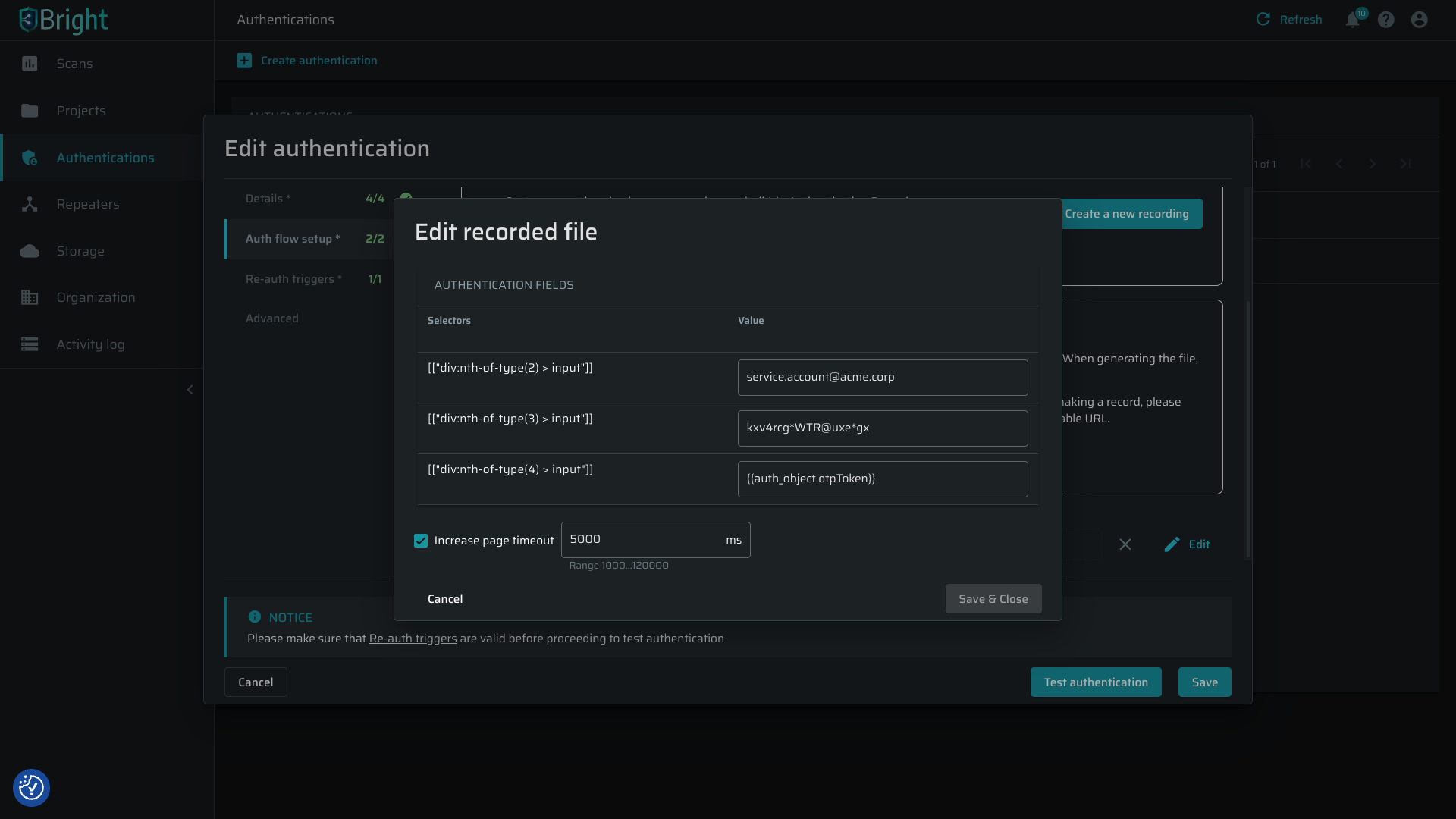
Edit recorded authentications
-
The recorded browser-based form authentication type helps users set up authentication objects by recording the login steps in the background using the Bright or Chrome recorder and capturing this in a JSON format. When authentication is required for the scanning, Bright will repeat these steps and log on to the application.
-
In this release, we’ve added options to edit your recorded files:
-
Field value: You can now edit the authentication field value, such as user name or password, In the Create/Edit Authentication dialog under the Auth Flow Setup tab.
-
Page Timeouts: Adjust how long each page waits before timing out (from 1 to 120 seconds) to address slow page loading speed.
-
One-Time Passwords: append one-time passwords (OTP) generated by the OTP Generation settings under the Advanced tab by entering the marker
{{auth_object.otpToken}}, replacing the static OTP saved by the page recording (e.g.763041). -
-
